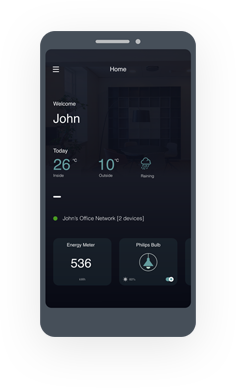
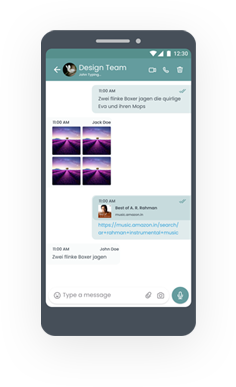
Developers and OEMs can not only create Apps and Devices installed in networks that are owned by users, but can also create Apps and Devices in networks that are owned by the Developer and OEM themselves. In this latter case, the data generated within the network is completely owned by them and can be used for aggregation. The users can transparently choose to give away their data in exchange for the services that you provide.
Apart from privacy, decentralized apps and devices can take advantages of edge computing, enable cost savings from cloud bandwidth reduction, low latency, real-time communication, remote and offline connectivity for the users, and reduced risk of data breaches,
The COCO platform provisions for SDKs and ready-made software libraries that reduce development cycles and costs.